Think Before You Click
You may have heard the buzz words: phishing, baiting, pretexting, business email compromise or tailgating in the world of Cybersecurity. These are all words for a type of computer fraud commonly referred to as Social Engineering.
Social Engineering is defined by Oxford as “the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes.” Sound like that’s hard to do? Think again.
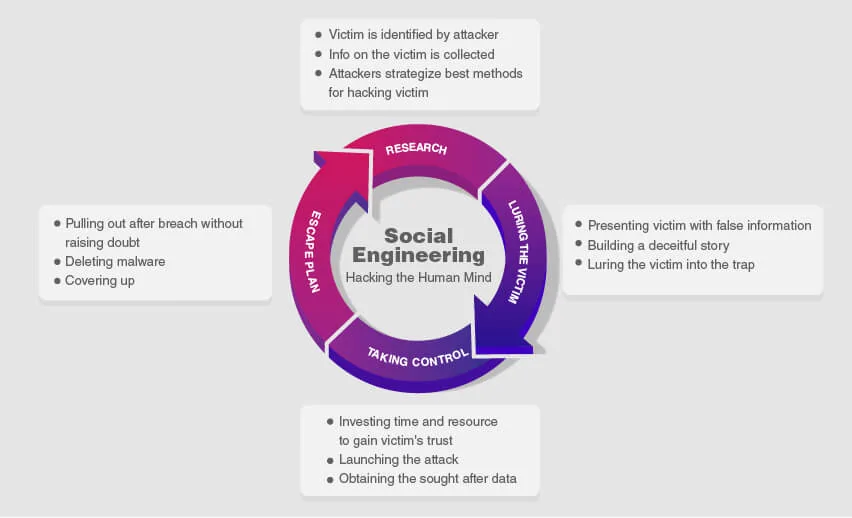
How Social Engineering Happens
Consider this – Cyber criminals do their homework before attacking. By trolling social media platforms and researching company websites, the criminal obtains employee email addresses and finds out the CEO is traveling out of town soon. An email is then sent to a company employee that portrays to be from the CEO. Upon first glance, the email address and the request look legitimate. The email asks you to transfer $250,000 to a new customer or a new bank account. You do not see anything unusual about the email, so you set up transfer of payment only to find out that the email was not actually from your CEO, it was from a cyber-criminal. A few days later you and the CEO realize that you have been victims of a Social Engineering attack.
Hackers not only use email to gain illegal access into your network, but also your phone, snail mail or direct contact. Social engineering unfortunately plays on the human instinct to trust others. These criminals are playing off that inherent trust and swindling more and more companies out of money. According to Forbes, the FBI released a statement that Cybercriminals stole $2.4 billion by compromising business email accounts in 2021 alone.
Forms of Social Engineering Attacks
Social Engineering attacks come in many different forms. The most common forms include:
- Baiting: Using false promise that lures users into a trap to capture their personal information through use of a portable storage media such as a USB. When the files are opened it executes malware that can release a virus.
- Scareware: False alarms and threats inflicted deceiving users to think their system is infected with malware. A common scareware is a pop-up that displays when you are web surfing stating “Your Computer has been infected. Click here to learn more.”
- Pretexting: Manipulating others into divulging sensitive information. Hackers ask for information under the guise of confirming their identity, when in fact this information is used for secondary threats or identity theft.
- Phishing: Fraudulent emails impersonating another individual or company to induce the release of personal information such as credit card numbers, banking information or passwords. According to EarthWeb, 3.4 billion phishing emails are sent out each day across the world.
- Spear Phishing: More targeted version of phishing whereby the attacker tailors a message to specific individuals impersonating a trusted sender to obtain confidential information.
Astonishingly, Cyber criminals use social engineering in 98% of attacks. According to Web tribunal, 75% of companies worldwide were victims of phishing in 2020.
Prevent Cyberattacks
A few of the safeguards you can put into place include:
- Carefully read any email address or website you encounter, checking for misspelled words.
- Don’t open emails, especially attachments from unknown and suspicious sources.
- Secure your devices with anti-virus software, firewalls, MFA, VPN and email filters.
- Be leery of any “offers” for something free after clicking a link.
- Keep antivirus software up to date.
- Never transfer money without dual control practices. If a request is sent via email follow up with a phone call to the sender directly. (Note, do not simply call the phone number referred to in the signature of the email received – instead, go to the main phone number on file for the company and be transferred to the associate directly).
- Set spam filters to “high” – just remember to check your spam folder periodically to confirm if a legitimate email has been caught.
- Train your employees. Run random phishing tests to see if your employees are fooled. Educate them on correct practices so it will not happen again. Since 95% of cyberattacks are attributed to human error, proper training can mitigate many losses.
Make Sure You Are Covered
Some insurance carriers will provide social engineering sublimated coverage through an endorsement to a Crime or Cybersecurity policy with limits up to $250,000. This can often be obtained by completing a supplemental application.
Social Engineering can impact an organization in many ways, including financial loss and damage to reputation. Over half of U.S. companies have experienced some sort of Social Engineering attack; which shows just how big of a threat this really is. Knowledge could be your greatest protection. Be sure to engage the experts at Sentinel to continue to Safeguard Your Success.